Using BurpSuite AI to Crack SQL Injection
Dynamic application security testing (DAST) has always been a bit of an art. Manual testers, bug bounty hunters, and pentesters spend hours crafting payloads, replaying requests, and analyzing subtle changes in responses all to uncover the one misconfigured query or unsanitized input that opens the door. But what if we could use generative AI to streamline some of that?
With the release of BurpSuite AI, PortSwigger is doing just that: layering AI assistance on top of their industry-standard security testing suite. I recently put it to the test using one of their own challenges: SQL injection vulnerability allowing login bypass from the Web Security Academy. Spoiler: Burp AI helped me identify and exploit the injection point faster than ever before.
Let’s dive in.
Why GenAI for Dynamic Testing?
Generative AI has already shown promise in secure code review, helping developers write secure code, and threat modeling. When it comes to dynamic testing where you’re interacting with live apps and interpreting responses in real time AI can serve as a powerful assistant:
Highlighting suspicious parameters
Recommending payloads
Generating explanations
Filtering false positives
And even creating login sequences
For busy AppSec teams or bug bounty pros juggling multiple targets, this saves hours per engagement.
BurpSuite: The Tester’s Best Friend
If you’ve ever done manual web app testing, you’ve probably used BurpSuite. It’s the go-to tool for intercepting, modifying, and replaying HTTP requests, with a built-in scanner and powerful extension ecosystem. PortSwigger’s reputation for quality tooling is well-earned, and they’ve steadily evolved Burp from a proxy-based interceptor to a full-fledged DAST solution.
With BurpSuite AI, they’re pushing into the next generation.
How BurpSuite AI Works
Burp AI integrates directly into BurpSuite Professional. It uses AI credits for its more advanced functionality, like vulnerability exploration and explanation. That means you’re not being billed per scan or minute, but per usage of AI-based features.
Here is a screenshot of the credit purchase:
Importantly, PortSwigger has emphasized privacy and control. Nothing happens without your explicit action. Your data isn’t used to train models, and you can inspect and customize prompts before sending. That said, there are trade-offs:
If you run out of credits, advanced AI features become unavailable.
Some features require manual review and verification before trusting results.
Case Study: Login Bypass via SQL Injection
For this test, I tackled this lab, which simulates a login form vulnerable to classic SQL injection. When you provide a single quote as the username, the application returns an HTTP 500 error response. This suggests it’s being used unsafely by the application, being interpreted as SQL, and breaking the authentication user query lookup.
Using BurpSuite AI, here’s how the workflow went:
1. Intercept the Request & Initiate a DAST Scan
After submitting the login form with dummy data, I intercepted the request in Burp Proxy. Seeing that it might be vulnerability, I launched a Burp Scan see what the scanner would find. Sure enough, it found a potential SQLi vulnerability.
2. Enable Burp AI
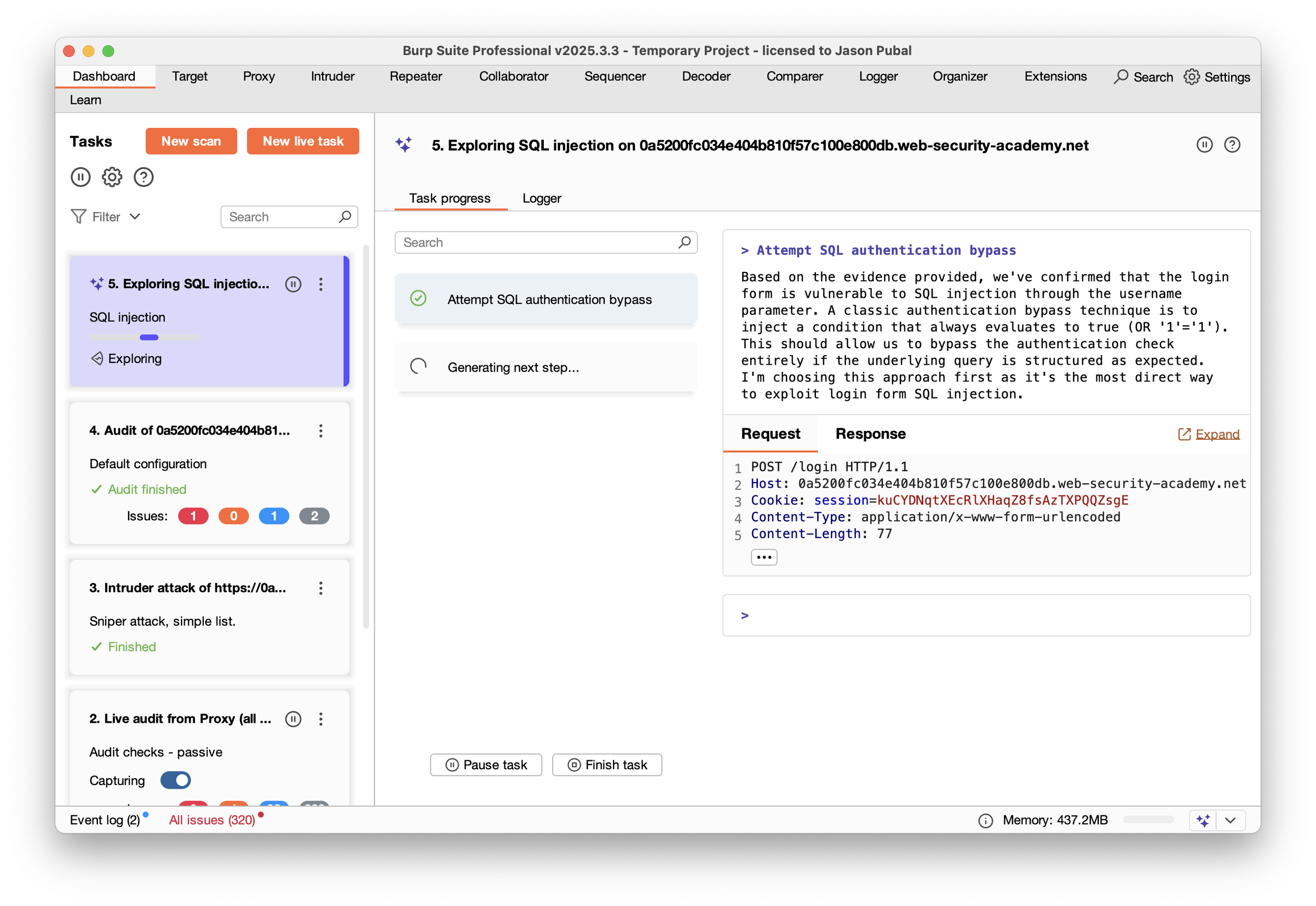
A ‘tentative’ issue in Burp needs further exploration to confirm. From the finding on the Dashboard, I launched the “Explore Issue” feature. Burp AI began analyzing the request, much like a manual penetration tester would, trying SQLi injection attacks that might exploit the authentication flow.
3. AI Suggested Payloads
Burp AI then suggested a payload:
' OR 1=1--
It’s first attempt didn’t work, so it tried another
administrator'--
Classic—but still valid. It automatically populated the parameter, sent the request, and confirmed that the login succeeded.
4. Explanation + Summary
Burp AI provided an explanation of the payload’s logic and confirmed that a SQL injection vulnerability existed, allowing login without credentials.
This not only saved time, but served as an excellent teaching moment, especially for junior analysts or those learning SQLi techniques.
This example used less than 200 AI credits, but more complex examples can quickly burn through credits.
Sure enough, that SQLi exploit successfully bypasses authentication and solves the challenge.
AI-Augmented Pentest Workflow
Here’s how AI-enhanced dynamic testing might look in practice:
Initial Recon – Use Burp’s crawler and passive tools
Authentication Setup – Let AI generate login sequences if needed
Scan + Manual Validation – Use traditional scan, then explore AI features to confirm, expand, or explain findings
Triage – Use AI to eliminate false positives and focus on exploitable issues
Report – Export AI-generated summaries as drafts for findings
Final Thoughts
BurpSuite AI won’t replace a skilled tester, but it’s a serious force multiplier. By guiding payload creation, filtering out noise, and speeding up common workflows, it’s making dynamic testing more accessible and efficient.
PortSwigger’s focus on privacy, transparency, and tight AI integration makes this a welcome addition to the AppSec toolbox. As AI models improve and integrations deepen, we’re likely to see tools like BurpSuite evolve into something even more collaborative and proactive.
If you’re doing manual testing, give it a shot, and let the AI do the heavy lifting when it can.